Continuous Zero Trust Platform
A security platform that delivers continuous zero trust access through centralized policy and a fully distributed enforcement architecture
Request a Demo
Simple, least-privilege, multi-cloud remote application access
Banyan's Continuous Zero Trust Platform is built on a patented Security Mesh archicture that transparently deploys and continuously enforces access policies based on any combination of user, device, and application context. The policies can be applied to the specific application, service or call anywhere on your multi-cloud access surface. Reduce relying on VPNs while simultaneously tightening your security posture and saving money.
Get the Whitepaper
What Banyan Zero Trust Continuous Platform provides
(that VPNs don't)
Fine-grained access controls
Delivers application-layer protocol and geo-location based access controls for both users and applications
Simple management and user experience
Eliminates management complexity of VPN appliances, and removes choke-points providing great user experience
Network-independent architecture
Enable homogenous policies across clouds, independent of network-layer technologies like VPCs and subnets
Incremental rollout for each application
Rollout to one application at a time, rather than an all-or-nothing VPN approach
Least-privilege, secure access
Unlike VPNs, no broad access grants at network-level that allow lateral movement to unauthorized applications
Reduced total-cost-of-ownership
No complex appliances to buy and manage policies for each cloud and region
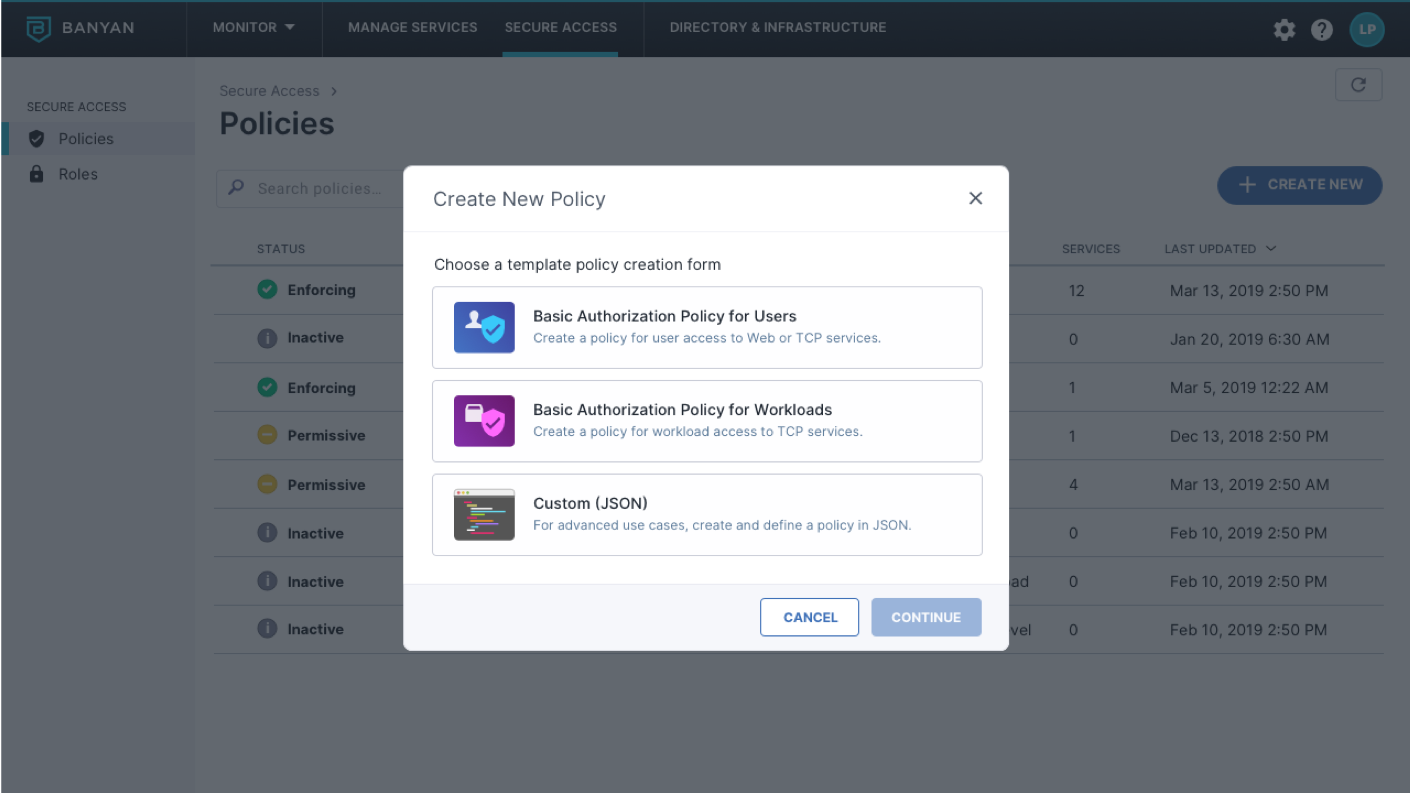
User, Device, and Application based Access Controls
Shift access controls away from the network, to perform continuous authorization based on user, device, and application context
- Distribute trust down to each individual user, device and application
- Define policies in terms of users and apps, with no need for deep networking knowledge
- Provide users least-privilege access rather than broad access to the network
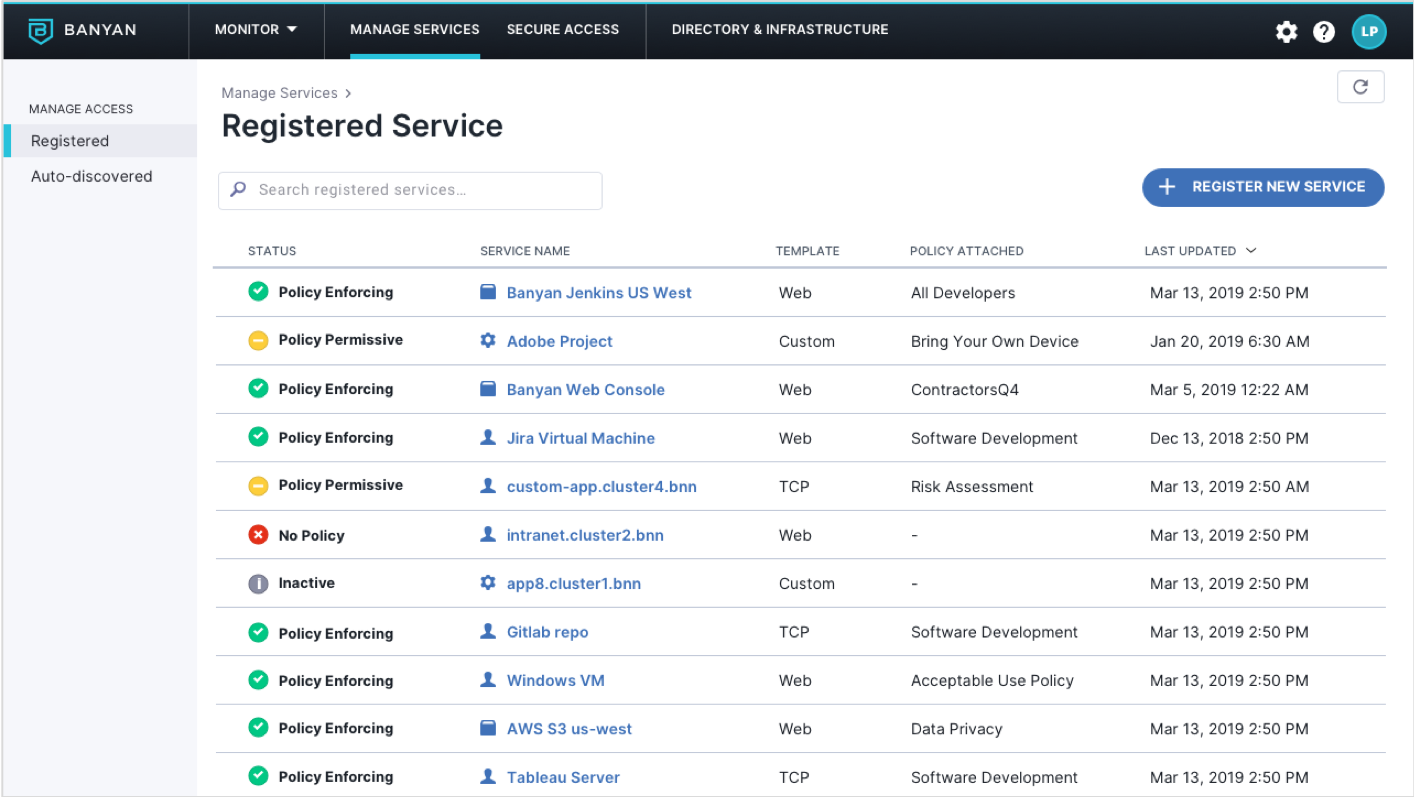
Always-On, Multi-Cloud Enforcement
Leverage a distributed mesh with virtualized security and compliance policy enforcement for scalable control across clouds
- Gain complete coverage across your multi-cloud access surface
- Resilient, high performance design with no single points of failure or data risk
- No appliances. No VPN clients, No extra hops. No choke points.
- Simple deployment & incremental roll-out
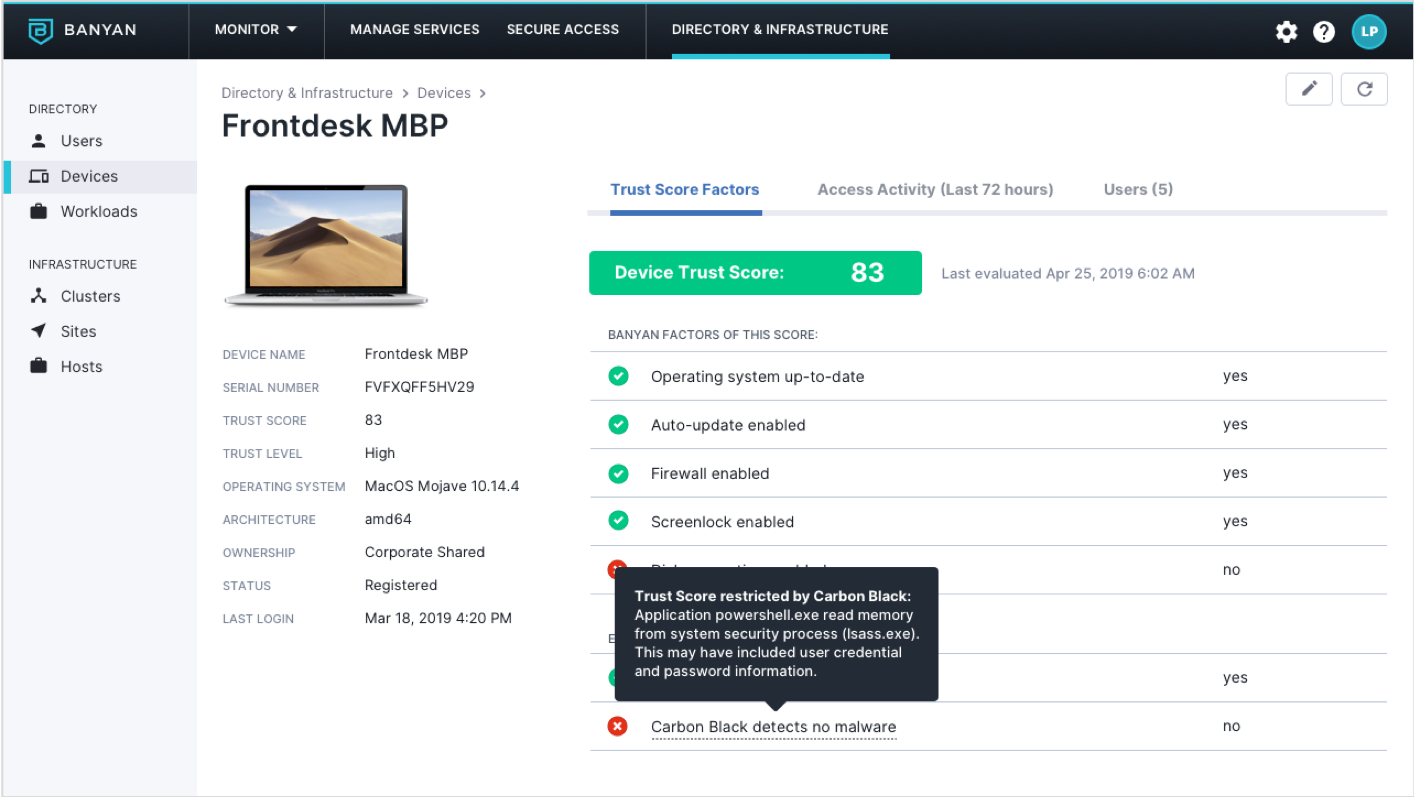
Real-time Visibility and Analytics
Interactively explore user and device access behavior, with intelligent alerting of actionable insights.
- Visualize all access patterns across your corporate applications
- Get notified of suspicious usage trends or malicious activity
- Deep-dive into connectivity for a specific user, device or application
On Demand, End-to-End Encryption
Automatically upgrade application connections to mutually authenticated TLS encryption, without making any changes to code or network.
- Go beyond the network perimeter; encrypt traffic end-to-end - all the way from the user’s device to the requested application’s server
- Traffic is encrypted on-demand, at the connection level, using short-lived cryptographic credentials
Access Surface Concealment
Don’t expose your sensitive corporate applications to the wild wild internet
- Hide internal application access points from crawlers and malicious probes
- Applications can only be reached by authenticated users on approved devices
- Protects against bot and DDOS attacks
Enterprise-grade Tooling and Workflows
Leverage your existing IT management systems as well as new DevOps processes.
- Integrate with your Cloud Platforms, Identity Providers and Enterprise Device Managers
- Easily incorporate into agile DevOps practices
- Utilize flexible APIs for ChatOps workflows
On Demand, End-to-End Encryption
Automatically upgrade application connections to mutually authenticated TLS encryption, without making any changes to code or network.
- Go beyond the network perimeter; encrypt traffic end-to-end - all the way from the user’s device to the requested application’s server
- Traffic is encrypted on-demand, at the connection level, using short-lived cryptographic credentials
Access Surface Concealment
Don’t expose your sensitive corporate applications to the wild wild internet
- Hide internal application access points from crawlers and malicious probes
- Applications can only be reached by authenticated users on approved devices
- Protects against bot and DDOS attacks
Enterprise-grade Tooling and Workflows
Leverage your existing IT management systems as well as new DevOps processes.
- Integrate with your Cloud Platforms, Identity Providers and Enterprise Device Managers
- Easily incorporate into agile DevOps practices
- Utilize flexible APIs for ChatOps workflows














